Malwarebytes provides a support tool that automatically repairs and fixes software issues and broken configurations, that’s actually common for anti-malware software to assist their customers to do that.
after navigation into HelpCenter inside the Malwarebytes interface, you need to download the software package which will do self-extraction and requires elevated permission to continue running.
since it requires such permission, I thought like other software it may dump the memory or something similar and that’s okay. but found more unexpected things to happen as the tool copies the HIVE files.
How does it happen?
after downloading and running the tool, the application interface comes with three options as the figure below

looking at the first option which is “Gather Logs” doesn’t indicate any attempt to access local PC account credentials, so I decided to give it a try and tune my Procmon filters to capture app activity.

figured out that, a newly dropped executable has been created into the local temp folder and executed after that
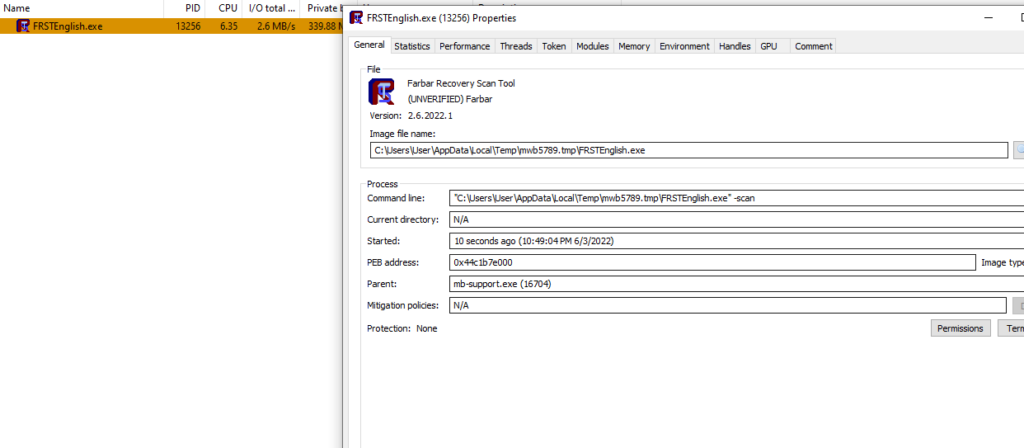
by doing some quick search, it comes it is an application (Farbar) used by Malwarebytes for troubleshooting and it is the one responsible for accessing windows HIVE.

Furthermore, the support tool doesn’t perform clean-up which could be abused in a way with leftover attacks to steal information. with tools such as samdump2, it’s easy to recover the NTLM hashes with the following command
samdump2 SYSTEM SAM
Addressing the risk?
the risk behind this could be categorized under left-over attacks or alternative ways to retrieve SAM, users with limited access permission can access and copy the content of the FRST folder created by “FARbar” or “MB support” tools.

offensive security expert and founder of 0xsp security research and development (SRD), passionate about hacking and breaking stuff, coder and maintainer of 0xsp-mongoose RED, and many other open-source projects

