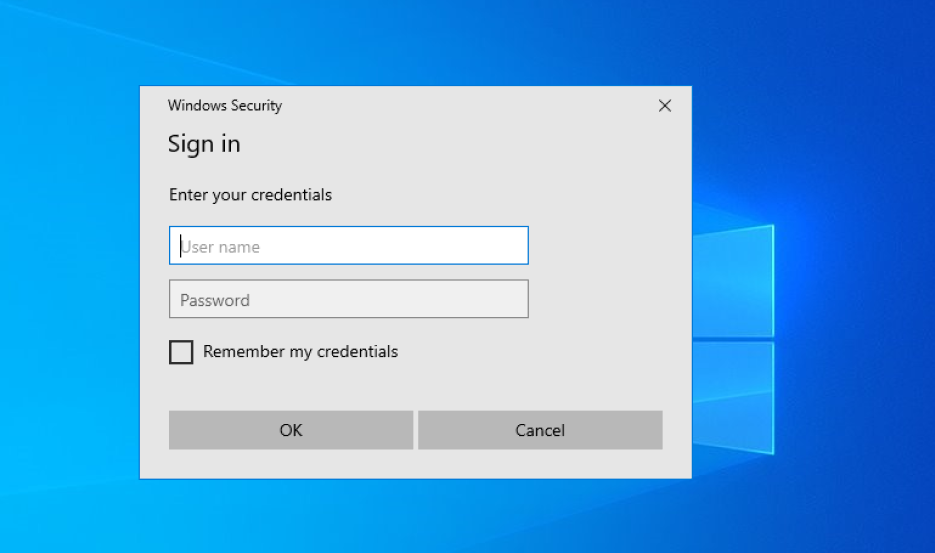
Navigating Embedded Payload Extraction from RDP Files – Defence evasion
Introduction This blog post will explore how to embed malicious payload into the RDP configuration file. By leveraging the innate properties of the file extensions and specific RDP configuration parameters, I have successfully injected malicious content without impeding the file’s intended functionality. Today’s topic delves into the technical details of this defense evasion technique and … Read more